Week 4: My First Step Toward World Domination
Maleea m -

Many of you reading this likely have one of these tucked away in an office or a central spot of your home. This is a Wireless Access Point (AP). It takes data from an Ethernet cable plugged into that oddly shaped outlet and turns it into a 2.4GHz or 5GHz wireless signal for all your IoT devices.
But here’s the thing, if a hacker gains access to your network, your AP becomes a goldmine for exploitation. Once inside, they can access all the IoT devices connected to it, from smart cameras and thermostats to voice assistants and even medical devices. Since many IoT devices have weak security by default hackers can take advantage of these vulnerabilities to launch attacks or steal sensitive data.
What starts as a single network breach can quickly escalate into a complete IoT takeover, putting both personal and corporate security at risk.
So of course, that’s exactly the thing I wanted to conquer.
Using FAT to Break In
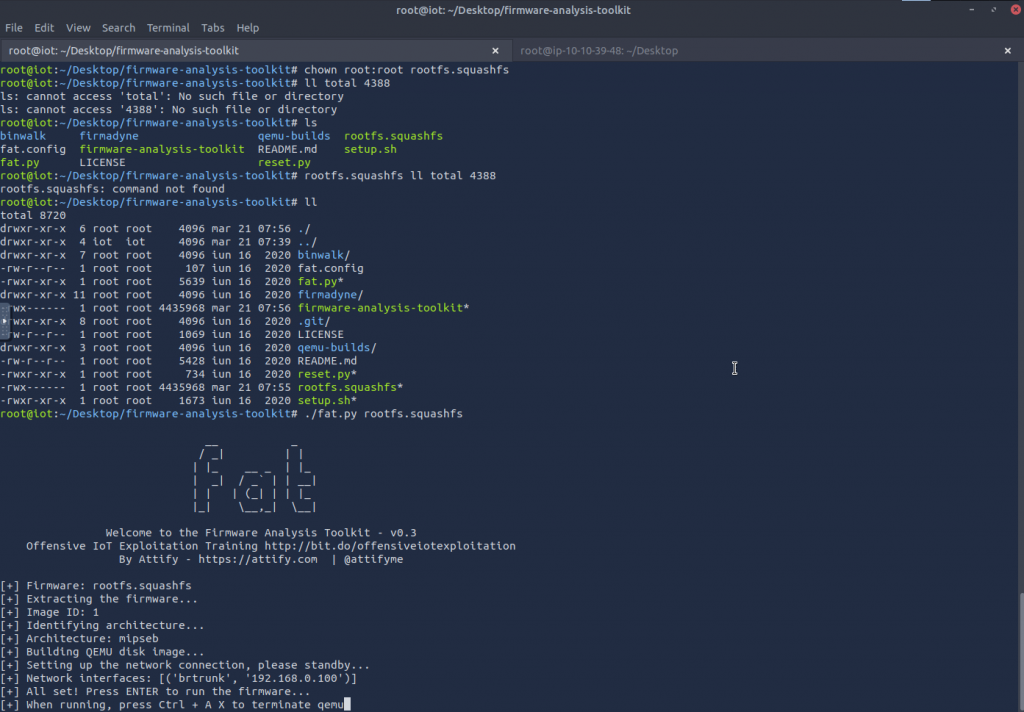
To begin my journey toward TOTAL (legal) HOME IOT DOMINATION (dun dun daaaaan), I needed a test subject: a virtual Netgear AP firmware from an outdated model, a perfect candidate for cracking.
Once I had the firmware in hand, the real challenge began: finding a vulnerability. This was like searching for a needle in a haystack, except each door I opened revealed even more doors, each stuffed with more hay.
At the bottom of the inserted snippet below is a list of 40~ files that control the device and its web application. The ones ending in “.php” (Hypertext Preprocessor) handle data processing. To find a vulnerability to exploit, I (the hacker 😎) would have to dig through more lines of code than anyone would want to count.

Thankfully, I had FAT, the Firmware Analysis Toolkit, my trusty sidekick in this digital treasure hunt. FAT scans through the firmware, identifying weak points and potential exploits, acting as my metal detector in my metaphorical haystack.
Proof of Concept: Exploiting the Web App
After skipping a few technical steps (to keep this clean), I finally gained access to the web application controlling the AP. But access alone wasn’t enough—I needed proof that I could manipulate it.
For my Proof of Concept (PoC), I injected “112233445566” into the MAC address field—an identifier that should only accept legitimate device addresses. If my exploit worked, running a ping command to the local host would cause a noticeable delay, proving the application was vulnerable to Command Injection.

And after a delay…
I was in.
–
While it’s important to be aware of the risks, there’s no need to panic. The good news is that there are simple, effective steps you can take to secure your network and IoT devices. Regularly updating your router’s firmware, changing default passwords, and using strong encryption like WPA3 for your Wi-Fi can go a long way in protecting your home or office from hackers. By staying informed and proactive, you can enjoy the convenience of connected devices without exposing yourself to unnecessary risks. Remember, cybersecurity is all about staying one step ahead, and with a few simple precautions, you can keep your digital life secure.
“Fun” Frightening Fact of the Week:
Cybercriminals have used compromised IoT devices, like smart cameras and routers, to launch massive attacks that disrupt entire networks and websites. In 2016, one of the largest DDoS (Distributed Denial of Service) attacks in history used over 100,000 hacked IoT devices to bring down major websites, including Twitter, Netflix, and Spotify.
The scariest part? Many of these devices had weak security, and most owners had no idea they were being used in the attack.

Comments:
All viewpoints are welcome but profane, threatening, disrespectful, or harassing comments will not be tolerated and are subject to moderation up to, and including, full deletion.